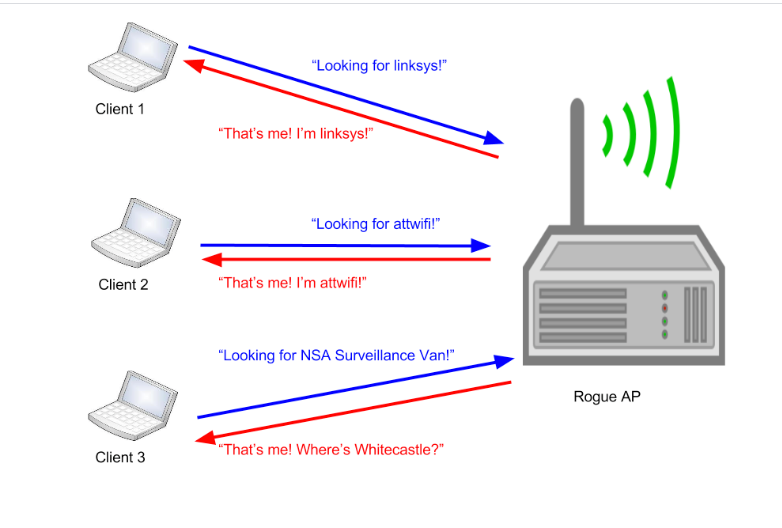
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members

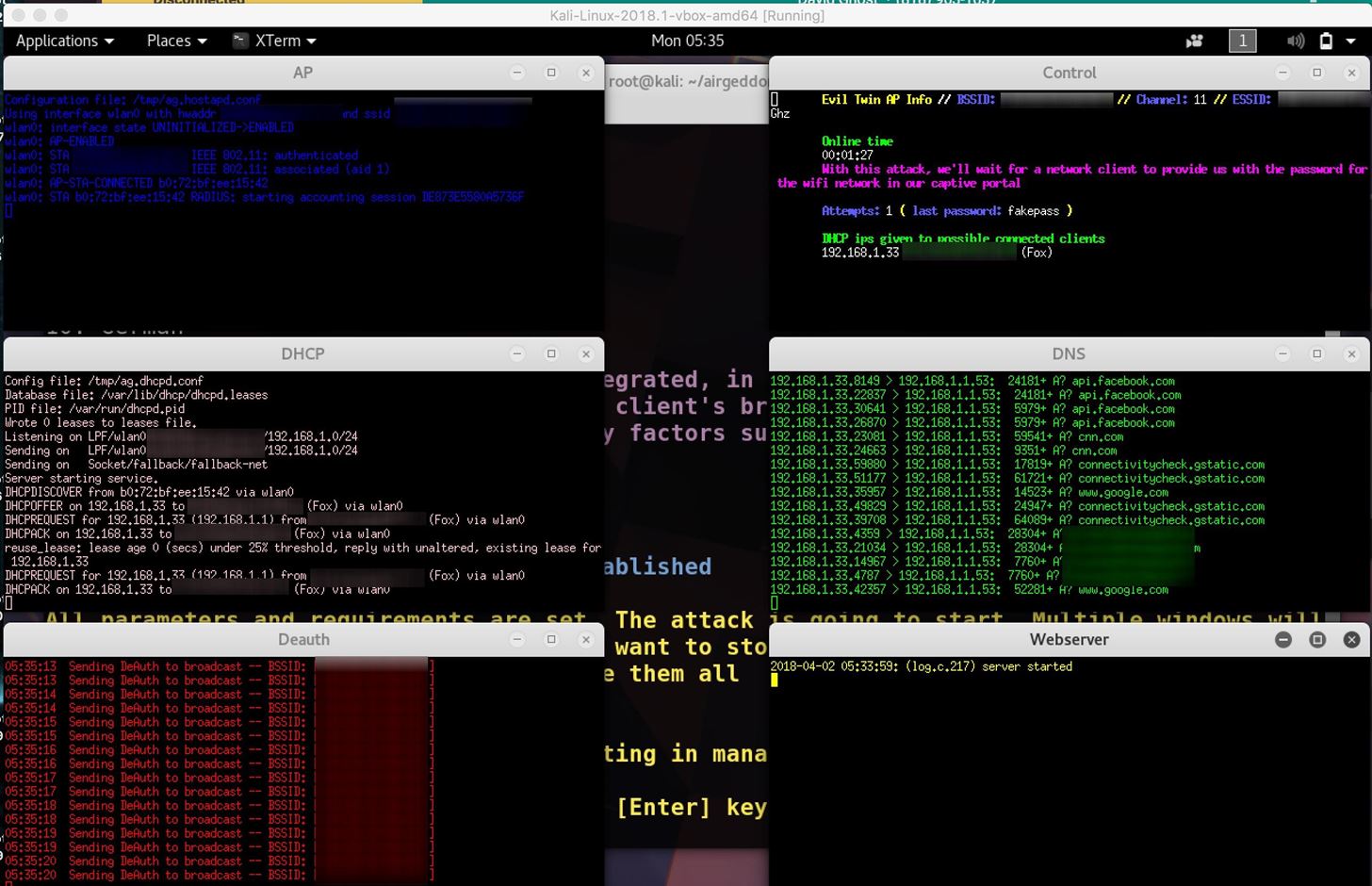
How to Hack Wi-Fi: Creating an Evil Twin Wireless Access Point to Eavesdrop on Data « Null Byte :: WonderHowTo

User 1 connects to the Internet through an evil twin. The number before... | Download Scientific Diagram




![PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar PDF] Evil Twin Attack Mitigation Techniques in 802.11 Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c7f8f05a26716f23022a0a028a628962a1a06612/2-Figure1-1.png)